Cryptography - Decipher the art of hidden communication !
🎯Concept Focus
Word origin: Crypto = secret; graphy = science of writing.
Definition: Science of transforming plaintext (PT) into ciphertext (CT) to achieve confidentiality, integrity, authenticity (and non-repudiation when signed).
Cryptography (algorithm + key)
Symmetric encryption: same key for encrypt/decrypt; fast for bulk data. Example: AES.
Asymmetric encryption: public/private key pair; public encrypts, private decrypts. Examples: RSA, ECC.
Key components
Algorithm: deterministic rules.
Key: secret value (e.g., binary 0101010) that drives the algorithm.
Encrypt PT → CT with an algorithm + key; decrypt CT → PT with the appropriate key.
Encoding vs Encryption (don’t confuse)
Encoding (character-level; usability/compatibility like ASCII/Base64): not a security control.
Encryption (binary-level; security): transforms PT → CT; requires a key to decrypt.
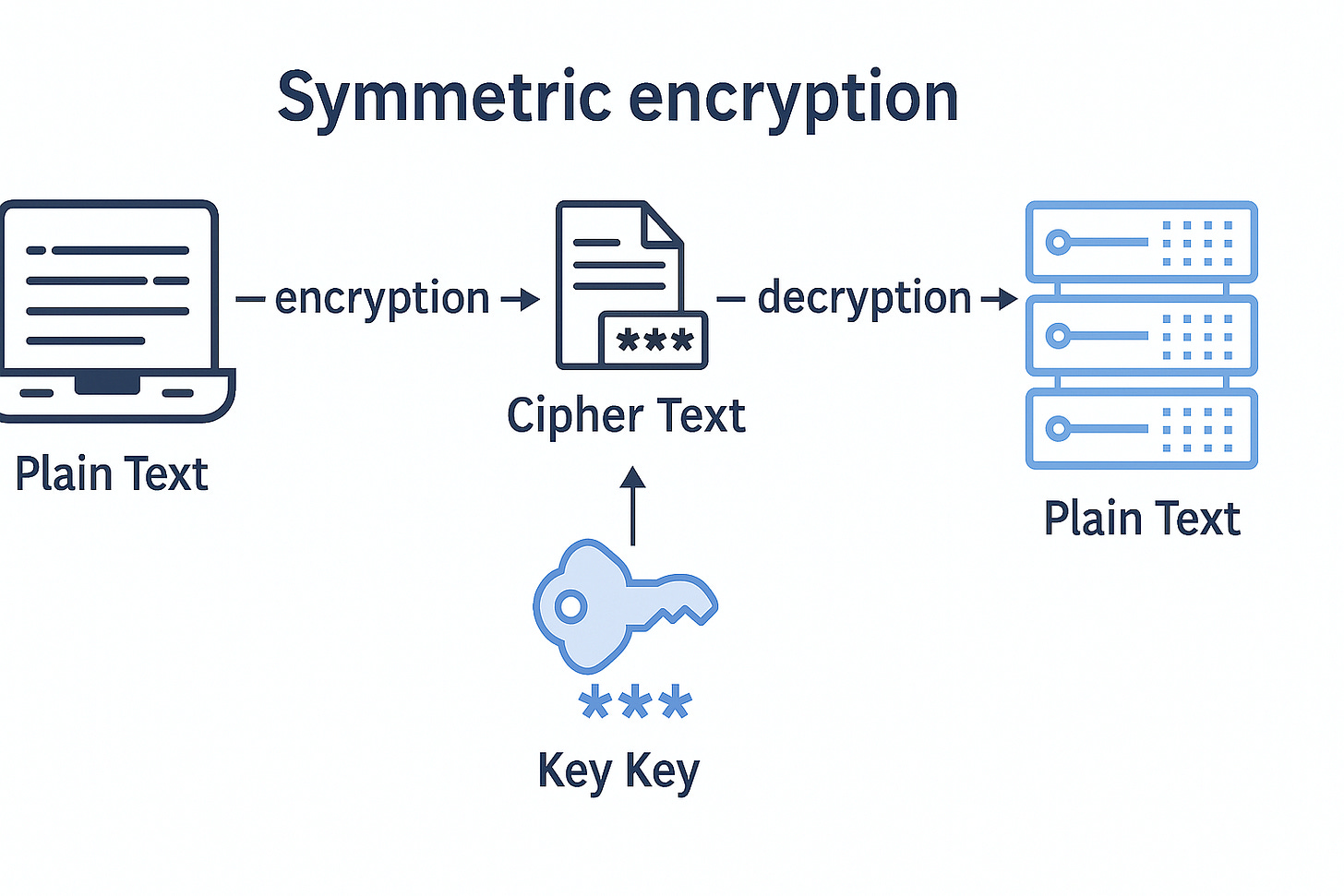
Symmetric Encryption
What it is
Single secret key (K) is used for both encryption and decryption.
Optimized for speed and bulk data (backup files, object storage, logs, telemetry).
Implemented as block ciphers (e.g., AES: fixed-size blocks, padding, modes) or stream ciphers (bit/byte-by-byte).
Why it’s fast
The operations (substitution, permutation, XOR, finite-field math) are constant-time and hardware-accelerable (AES-NI).
No expensive big-integer math per message like RSA.
Critical moving parts
Key (K): high entropy, KDF/PRNG generated, stored in KMS/HSM, rotated.
IV/Nonce: uniqueness prevents pattern leakage (e.g., CTR/GCM requires a never-reused nonce per key).
Mode of operation: ECB ❌ (pattern leaks), CBC (needs random IV; error propagation), CTR (nonce+counter; parallelizable), GCM (AEAD: adds integrity via authentication tag).
Padding: for block alignment (PKCS#7 etc.) when using block modes that require it.
How does Symmetric Encryption Work?
From key generation to decryption, multiple steps are involved when symmetric encryption is applied. These are the steps involved in sharing a message securely over the network using the symmetric encryption technique.
1. Key Generation:
The first step involves selecting a private key. A secure key is generated using algorithms like PBKDF2 (Password-Based Key Derivation Function 2) or hardware random number generators. This key must be securely shared or transferred over the network for future use.
Example: A 256-bit AES key: 3A7F2B4E... (32-byte hexadecimal string).
2. Encryption:
In this step, the original message (plain text) is transformed into unreadable text (ciphertext) ,and the plaintext is processed in blocks or streams using an encryption algorithm and the secret key.
Example: AES-256 in CBC (Cipher Block Chaining) mode encrypts a 128-bit block of plaintext with the key and an initialization vector (IV) to produce ciphertext.
3. Transfer of Cipher text:
The encrypted message (ciphertext) is then sent over the network. Even if intercepted, it remains unreadable to the attacker unless they have access to the shared secret key and the algorithm used for encryption.
4. Decryption:
In the final step, the recipient uses the same secret key and a reverse encryption algorithm to convert the cipher text back into the original message (plain text).
Risks to avoid
Key reuse across environments.
IV/nonce reuse (catastrophic in CTR/GCM).
Storing keys in code or CI variables.
ECB for structured data (images, JSON with repeated fields).
Read more at links
https://www.geeksforgeeks.org/ethical-hacking/what-is-a-symmetric-encryption/
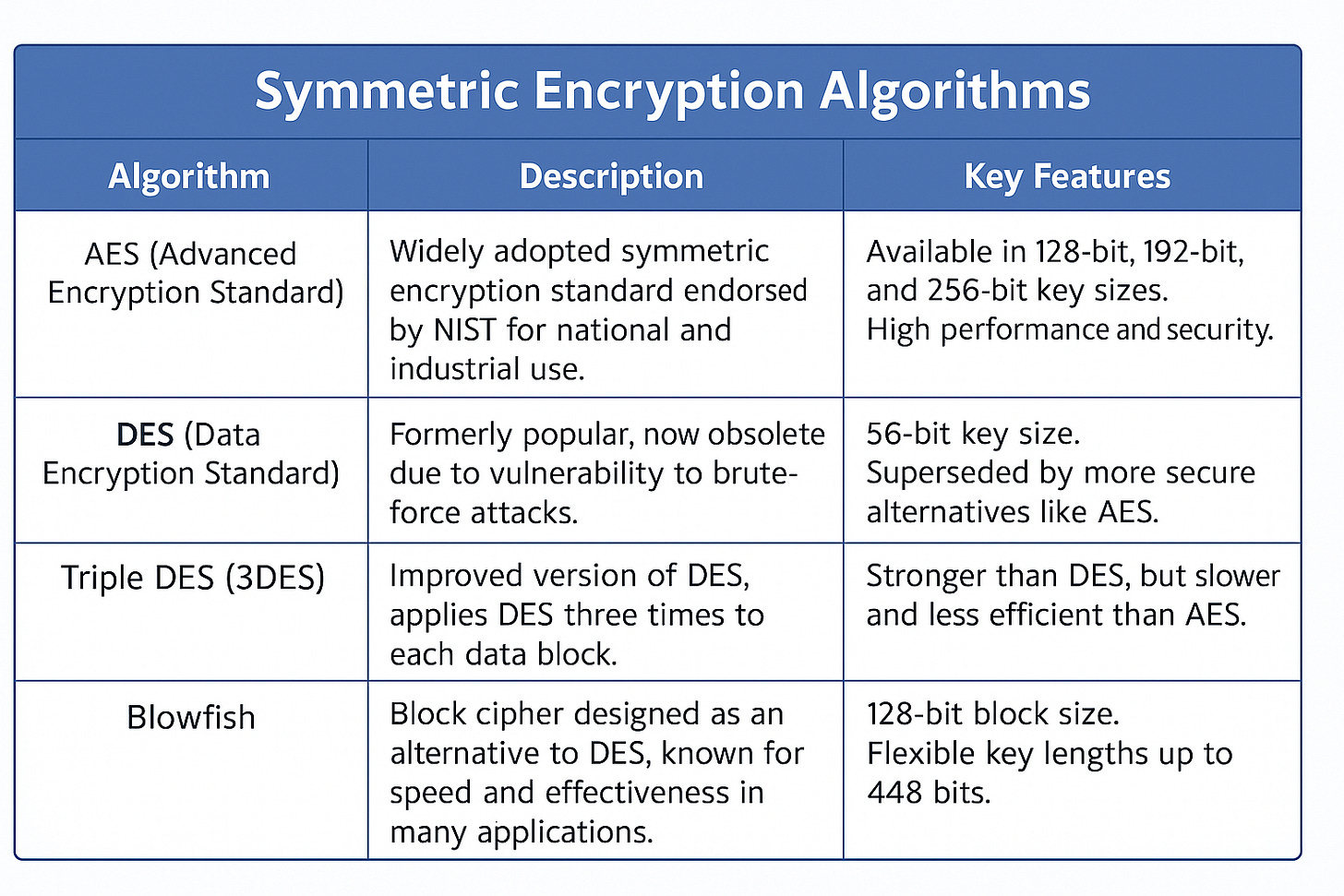
Symmetric Algorithms
Asymmetric Encryption
What it is
Two mathematically related keys: Public key (Pub) and Private key (Priv).
Confidentiality mode: Encrypt with recipient’s Pub, decrypt with recipient’s Priv.
Authentication/Signature mode: Sign with sender’s Priv (over a hash), verify with sender’s Pub.
Algorithms: RSA (factoring hardness), ECC (elliptic-curve discrete log), ElGamal (bigger ciphertexts), DH/ECDH (key exchange only).
Strengths
Solves key distribution (no sharing of private key).
Enables digital signatures, certificates, PKI.
Trade-offs
Slower than symmetric for bulk data → used to exchange a session key (hybrid).
Requires PKI (CAs, CRLs/OCSP) to vouch for public keys.
Side-channel risks (e.g., timing attacks on RSA) → use constant-time libraries/HSM.
Read in Detail at below links
https://www.geeksforgeeks.org/computer-networks/what-is-asymmetric-encryption/
https://www.haikel-fazzani.eu.org/blog/post/comparing-asymmetric-encryption-algorithms-cryptography
https://www.geeksforgeeks.org/computer-networks/asymmetric-key-cryptography/
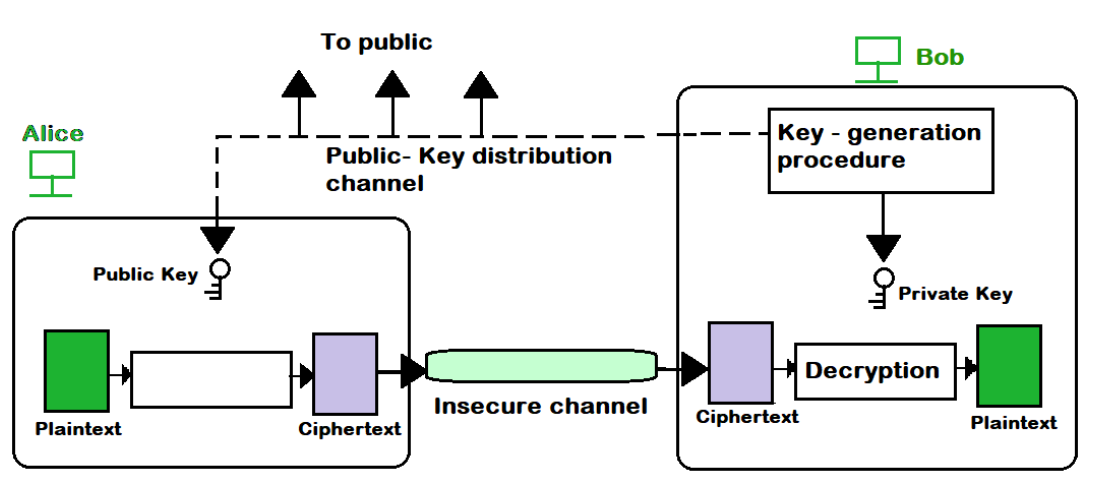
How does Asymmetric Encryption work ?
Asymmetric Encryption flow Diagram
1. Key Pair Generation:
The first step in asymmetric encryption is generating a pair of keys: a public key and a private key.
The public key is shared openly, while the private key is kept secret.
2. Encryption:
The sender uses the public key of the recipient to encrypt the message.
The public key is used because it is freely available and can be used to convert the message into an unreadable format (cipher text).
3. Transmission:
The encrypted message (cipher text) is sent over the network to the recipient. Even if intercepted by someone, it remains unreadable without the corresponding private key.
4. Decryption:
Upon receiving the encrypted message, the recipient uses their private key to decrypt it.
The private key is kept secure and is never shared, ensuring that only the intended recipient can decrypt and read the message.
5. Verification (Digital Signature):
In some cases, the sender may also sign the message using their private key to ensure its authenticity.
The recipient can verify the signature using the sender's public key, confirming that the message was not tampered with and was indeed sent by the intended sender.
6. Result:
Once decrypted, the message is returned to its original form (plain text), and the recipient can read it.
This method ensures both the confidentiality of the message (by using the recipient’s public key) and the integrity and authenticity (via digital signatures using the sender’s private key).
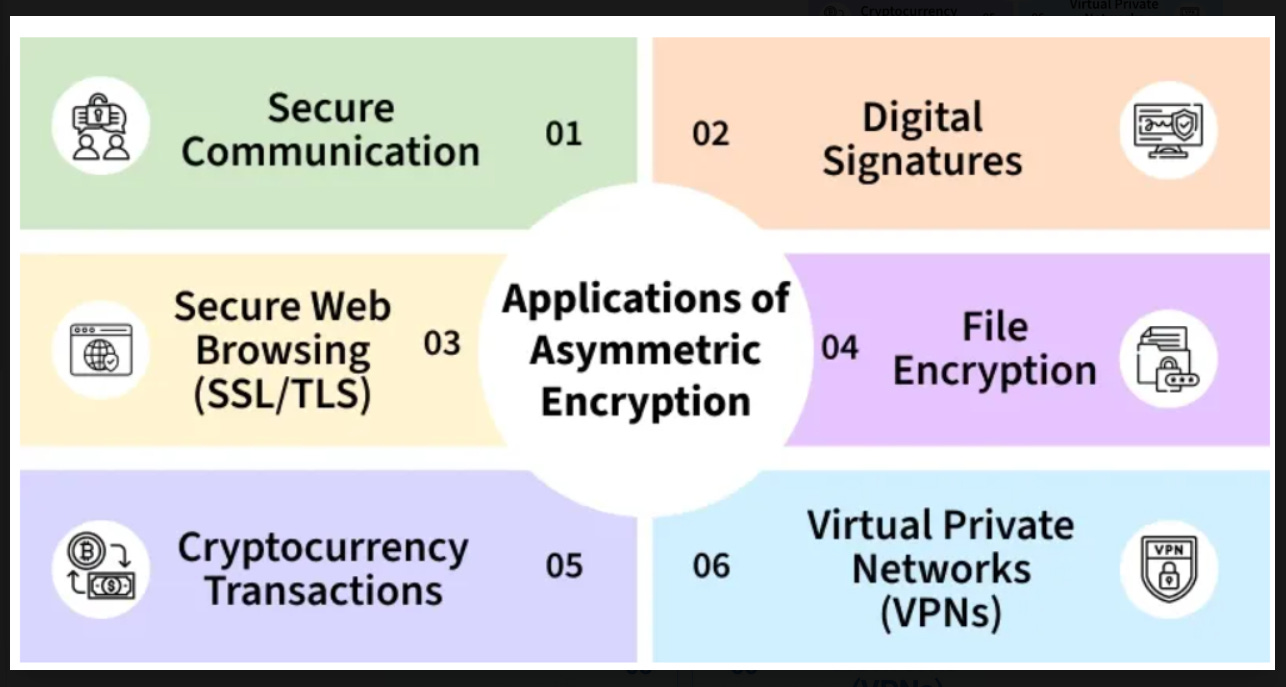
Uses of Asymmetric Encryption
(Image from GeeksForGeeks.com)
Asymmetric Encryption & The CIA Triad
1. Confidentiality
Goal: Protect information from unauthorized disclosure.
How asymmetric helps:
If Anya wants to send a payroll file to Marcus securely, she encrypts it with Marcus’s public key.
Only Marcus’s private key can decrypt it. Even if an attacker intercepts the ciphertext, they can’t read it without the private key.
👉 Example: PGP (Pretty Good Privacy) for secure email.
2. Integrity
Goal: Ensure the message hasn’t been altered in transit.
How asymmetric helps:
Marcus can create a digital signature by hashing the file and encrypting the hash with his private key.
When Anya receives it, she uses Marcus’s public key to verify the signature. If even a single bit was changed, the hash check fails.
👉 Example: Code signing for software updates.
3. Availability
Goal: Ensure authorized users can access data when needed.
How asymmetric helps (indirectly):
By supporting TLS handshakes on the web, it enables secure sessions for banking, HR portals, or test automation dashboards at Neuromesh.
Without it, attackers could impersonate services (spoofing), making systems unreliable or unsafe to use.
While asymmetric encryption itself doesn’t guarantee uptime, it builds trustworthy channels that prevent denial-of-service via impersonation.
👉 Example: HTTPS certificates issued via asymmetric cryptography.
🔄 Neuromesh Analogy
At Neuromesh:
Anya wants to send test logs to Anas (IT admin).
She encrypts with Anas’s public key → ensures confidentiality.
Anas signs his response with his private key → ensures integrity.
Both rely on TLS for their collaboration tools to stay available → supports availability.
🧠 Brain Ticklers
Q1. Anya needs to encrypt a 5 GB log file before uploading it to Neuromesh’s storage. Which method is most efficient?
A. Asymmetric encryption (RSA) with 2048-bit key
B. Symmetric encryption (AES-256) with shared keyK1
C. Encoding with Base64 before upload
D. Signing with Neuromesh’s private key
Q2. Marcus tells Anya to “never email a symmetric key over the internet.” Why?
A. Keys can only be exchanged in Base64 format.
B. If the symmetric key is intercepted, the entire system is compromised.
C. Symmetric keys regenerate automatically, so distribution is irrelevant.
D. Asymmetric encryption does not require keys at all.
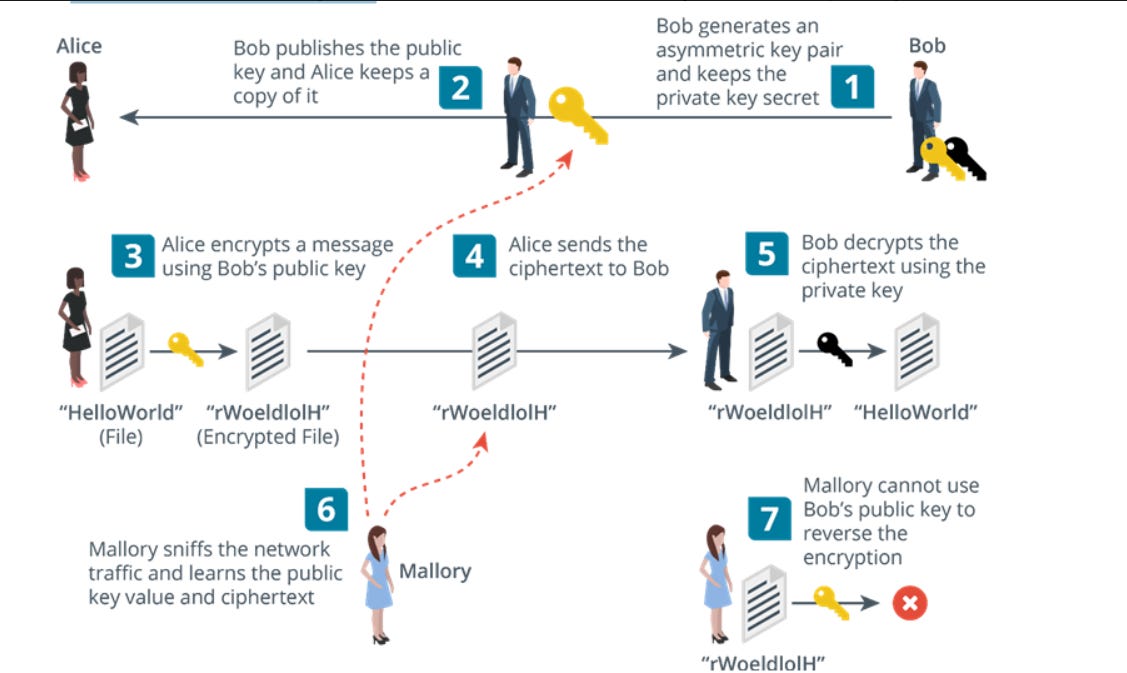
Q3. In the uploaded diagram (Alice → Bob), why can’t Mallory use Bob’s public key to decrypt the ciphertext?
A. Public keys are designed for decryption only.
B. Mallory intercepted the ciphertext incorrectly.
C. Public keys can only encrypt; private keys are required to decrypt.
D. Mallory needs Anya’s public key instead.
Q4. Neuromesh wants both confidentiality and authentication in their API communication. Which combination is correct?
A. Encrypt with Bob’s private key, decrypt with Bob’s public key.
B. Encrypt with Bob’s public key (confidentiality), sign with Anya’s private key (authentication).
C. Encrypt with Base64, verify with SHA-1.
D. Encrypt with AES, publish the AES key on GitHub.
Follow the Series - Virtualization & Cloud
#CISSP #CyberSecurity #InfoSec #SecurityLeadership #WomenInCyberforce #WomenInTech #AnyaInCyberSecurity #FromDevToDefender #TechLeadership #DevSecOps #CISSPDomains #Cryptography #AES #RSA #ECC #TLS #KeyManagement #Governance