Physical Security, the First Firewall
🎯 Concept Focus — What CISSPs must know about Physical Security (Domain 3)
Physical security is the bedrock of availability and the first layer of defense-in-depth. If someone can walk to your rack, they can walk through your controls.
Led by physical security specialists (facilities, guards, integrators), not IT—yet it must interlock with cyber.
Designed around deterrence, delay, detection, assessment, and response (DDDAR).
Implemented through site design, perimeter controls, building controls, room/zone controls, and people/process.
Why it matters :
You must evaluate risk reduction from locks, cameras, barriers, and drills.
You must translate tech risk into facilities action (“This server room needs fail-secure, two-person rule”).
You must catch information-security impacts of weak physical controls (e.g., “open wiring closet on Level 3 = unlogged access to core switch”).
CPTED (Crime Prevention Through Environmental Design) in one breath:
Shape behavior with the space itself—natural access control (fewer, guided entries), natural surveillance (see and be seen), territorial reinforcement (clear ownership cues). Add target hardening when needed (locks, bollards, laminated glass).
How to reason about the site
Defense-in-Depth Zones
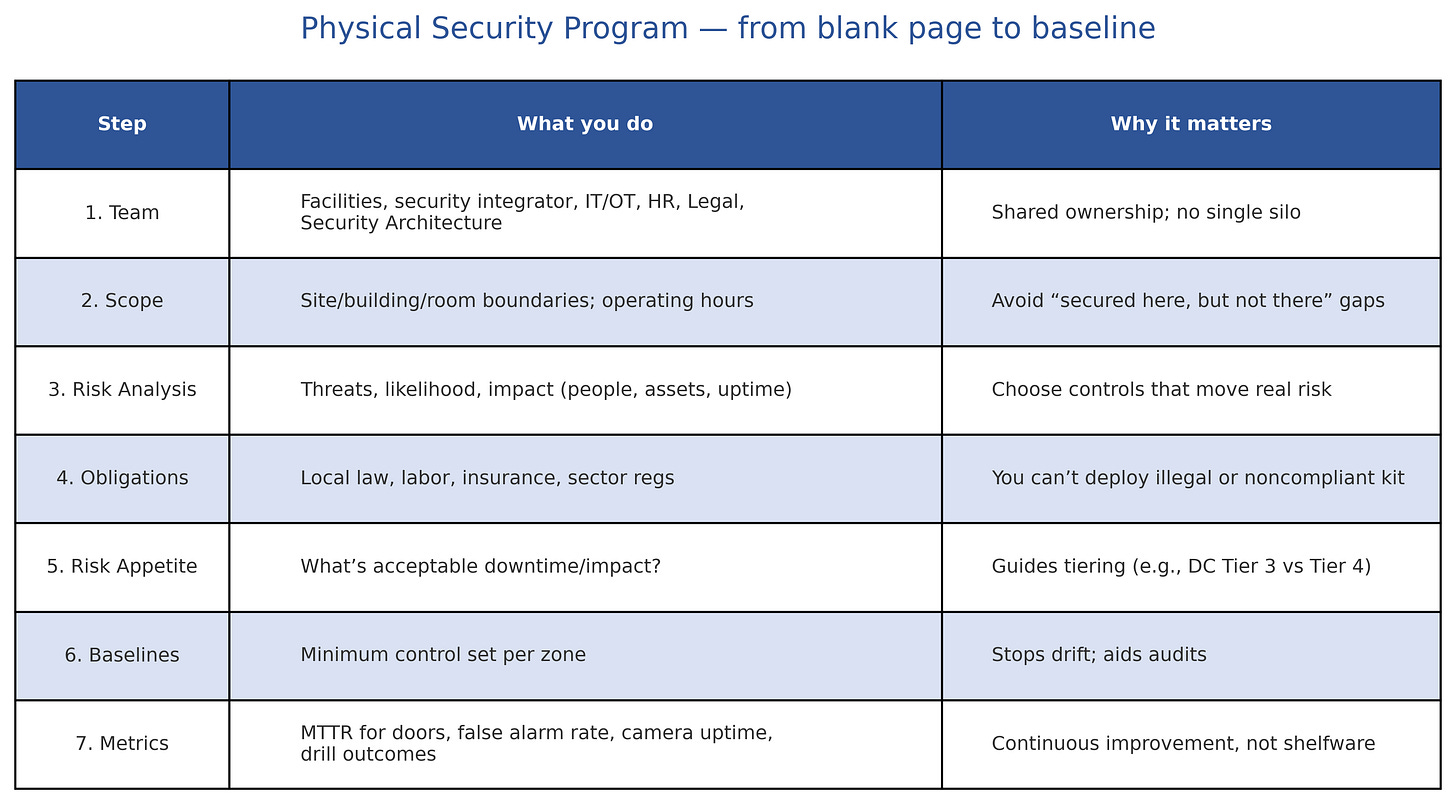
Physical Security Program — from blank page to baseline
CPTED quick hits for Neuromesh HQ
Limit entry points (fewer doors, better monitored).
Guide with landscaping & paths; light all walkways.
After hours: collapse to one staffed/monitored entrance.
Reception discipline: no badges, no entry; visitors always escorted.
Territorial cues: floor decals, color bands, “Staff Only” lines—make boundaries obvious.
Windows & Glass
Avoid door-adjacent windows; use laminated or BR glass for sensitive zones.
Ground windows: fixed, non-operable.
Magnetic switches + glass-break (dual-tech: acoustic + shock).
Steel frames where it counts.
Perimeter & Barriers
Fixed bollards for anti-ram; chicanes/speed tables to slow vehicles.
Deployable bollards for threat level changes.
Fences that deter but don’t blind cameras; consider hostile planting (thorny hedges).
Internal Controls
Door policy: fail-safe for life safety exits, fail-secure for high-value rooms.
Mantraps at data center. MFA for physical access (card + PIN/biometric).
Two-person rule for racks, evidence rooms.
Logging & video tied to badge events; alert on door-held-open.
Site selection (new leases, new DCs)
Visibility & neighbors: avoid high-risk adjacencies (chem plants), check crime stats.
Emergency proximity: police/fire/medical within SLA.
Access: roads, congestion patterns, airport/rail (balance logistics vs threat).
Natural hazards: floods, snow, seismic; stack wiring closets vertically in towers.
Data Center & Server Rooms
No windows, single controlled entry, central in building, seismically braced racks.
UPS (ride-through) + generators (load carry). Uptime Institute tiers:
Tier 1 (basic), Tier 2 (some redundancy), Tier 3 (N+1), Tier 4 (2N).
HVAC sized for load with redundancy; target 18–21°C, ~50% RH; manage rate-of-change.
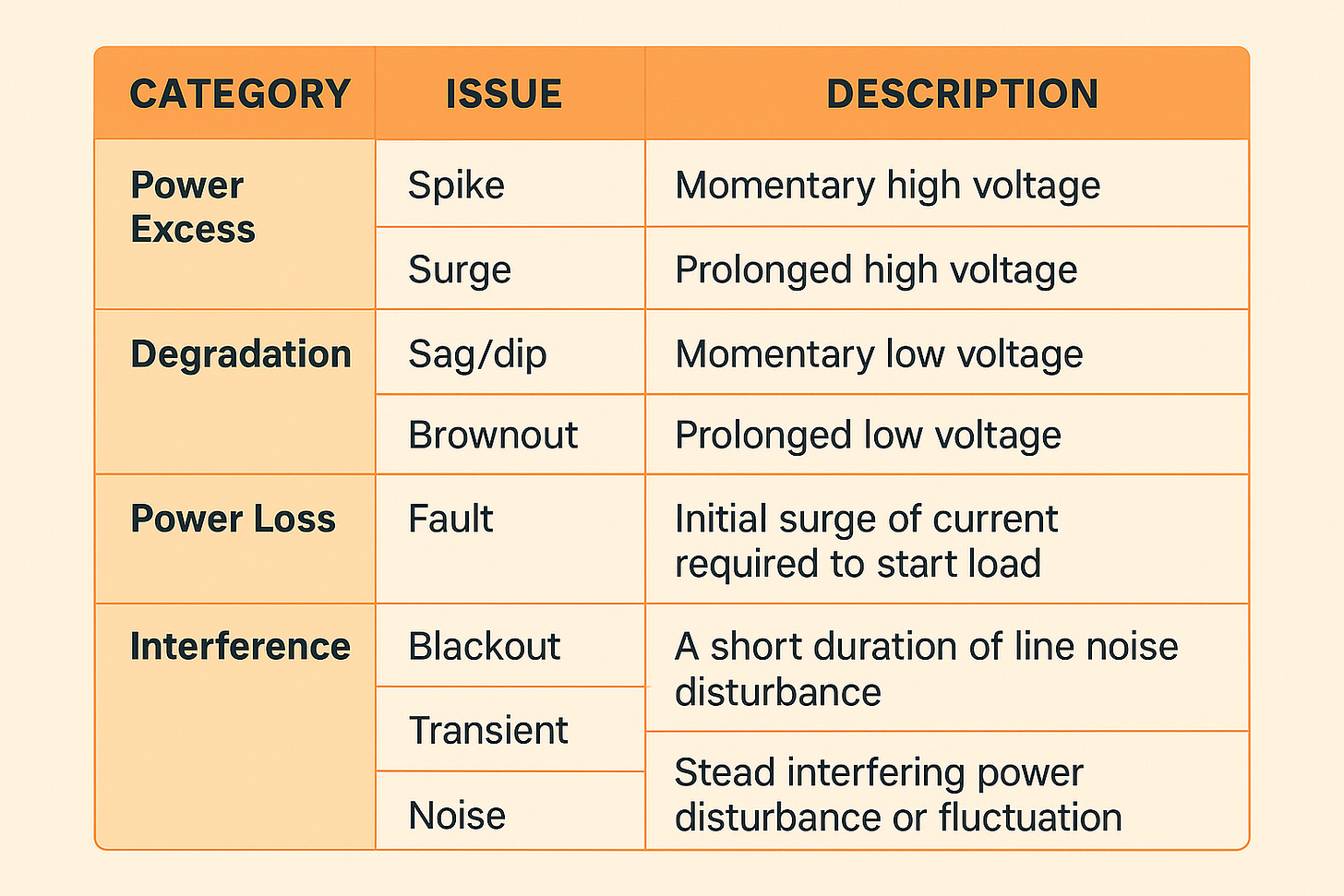
Power quality if “noisy” electrical neighbors (motors, compressors).
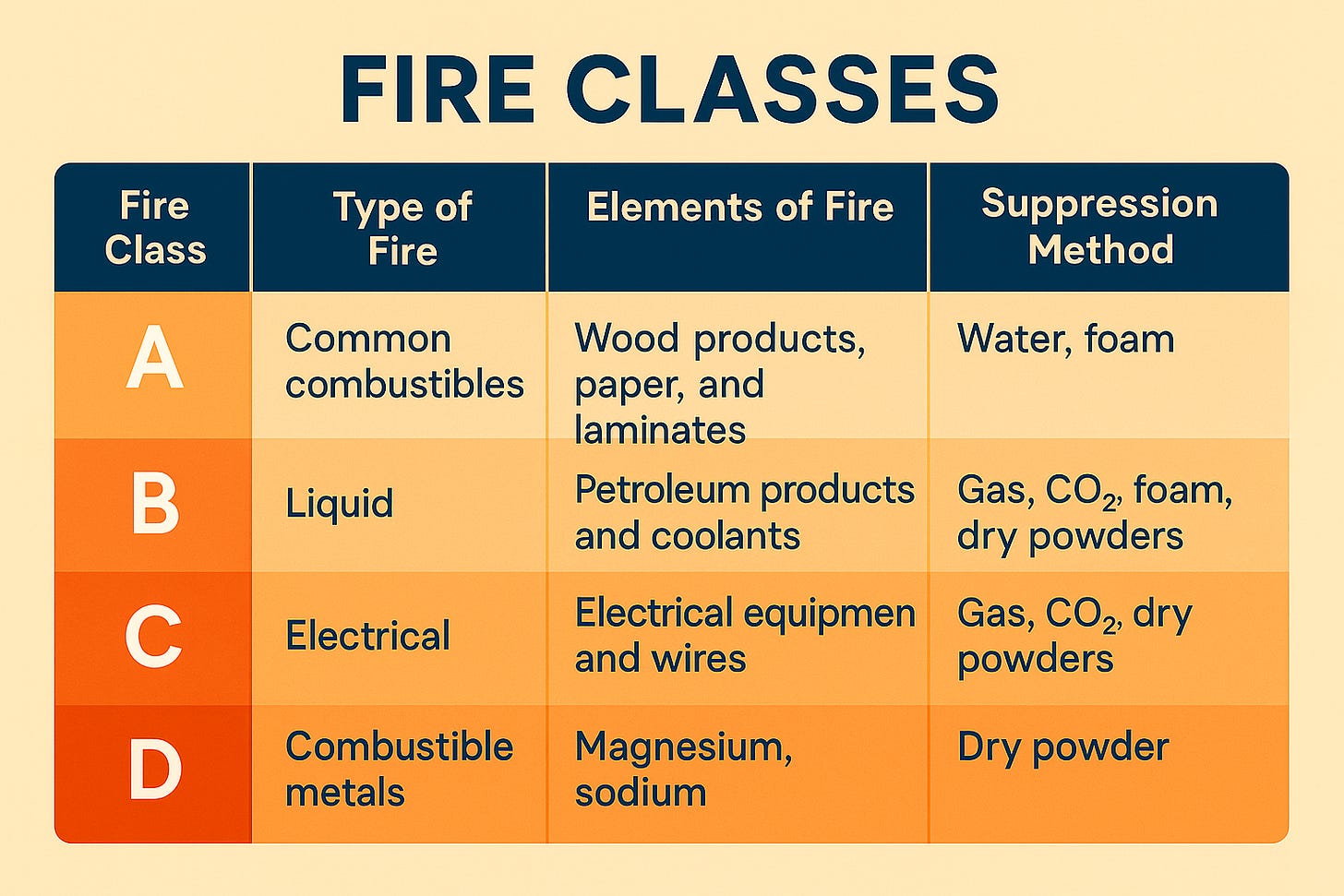
Fire — detect early, suppress smart
Stages: Incipient → Smoke → Flame → Heat
Detectors: Ionization (incipient/flaming), Photoelectric (smoldering), IR flame, Thermal (fixed / rate-of-rise)
Placement: above ceilings, under raised floors, in returns/vents.
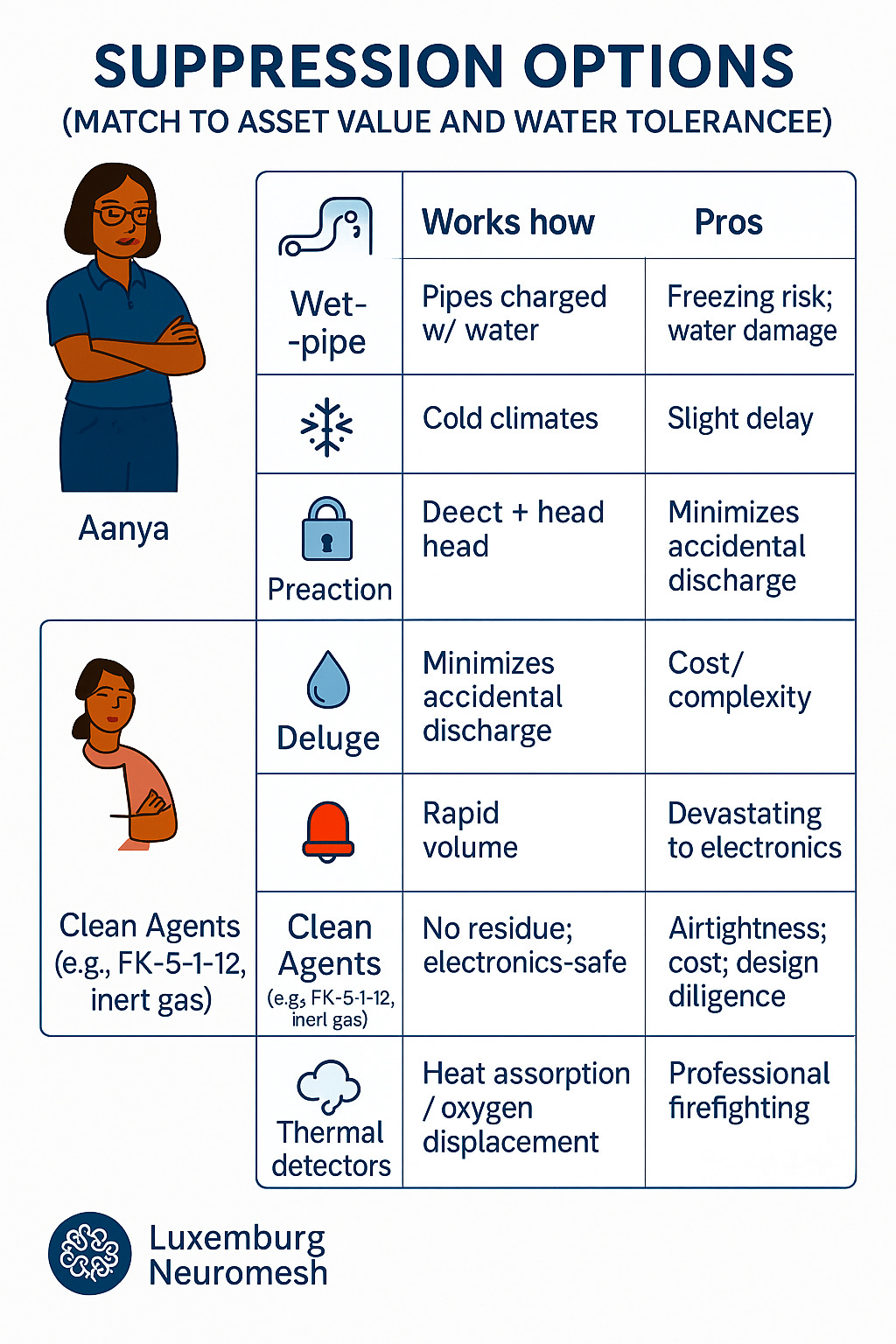
Human safety stays first: CO₂ needs pre-discharge alarms and evacuation procedures.
How Anya ties it together
Perimeter: Add bollards at the loading dock; lighting audit and replacements; camera overlap to eliminate blind turns.
Lobby: Replace swing gate with anti-tailgating turnstile, enforce visitor escort, and stop “badge-borrowing” with random guard checks.
Floors: Add readers to wiring closets; set door-held-open alarms to 30 seconds with SOC tickets.
Server Room: Switch to fail-secure, add mantrap, require card + PIN + biometric; implement two-person rule; upgrade to preaction + early smoke detection.
Process: Quarterly access reviews (HR + IAM), evacuation drills, generator/UPS full-load tests, and camera uptime metrics in the security scorecard.
CPTED sweep: Reduce after-hours entry points to one; guide foot traffic with lighted paths; territorial signage on every restricted door.
Anya’s conclusion to Marcus: “We keep talking about ‘north–south’ and ‘east–west’ traffic. Today we learned about ‘outdoor–indoor’ traffic. The building is part of the network.”
🧠 Brain Ticklers
Q1. A courier tailgates into Neuromesh’s lobby during lunch rush. Which primary DDDAR goal was weakest?
A. Deterrence
B. Delay
C. Detection
D. Assessment
Q2. The server room door should stay locked during a power outage, but life safety for exits elsewhere must be preserved. What combination is correct?
A. Fail-safe everywhere
B. Fail-secure everywhere
C. Fail-secure for DC, fail-safe for emergency egress
D. Fail-safe for DC, fail-secure for egress
Q3. Neuromesh adds glass-break sensors to a conference wall facing the corridor. Which most robust configuration reduces false negatives?
A. Acoustic only
B. Shock only
C. Dual-tech (acoustic + shock) with proper placement
D. Video analytics instead of sensors
Q4. Anya proposes preaction sprinklers for the DC. What is the most accurate rationale?
A. They’re cheapest and fastest to install
B. They discharge water immediately on smoke detection
C. They require detection and heat at the head, reducing accidental discharge risk
D. They eliminate the need for clean agent systems
Q5. Which is the best CPTED improvement for after-hours at Neuromesh?
A. Keep all doors open to allow ventilation
B. Reduce to a single, monitored entry and guide approach with lit paths
C. Turn off lighting to save power
D. Replace turnstiles with rope barriers
Takeaways for busy readers
Buildings are networks. Treat entries as trust boundaries with logging, MFA, and metrics.
DDDAR > check boxing. Design for Deterrence, Delay, Detection, Assessment, Response as a chain.
CPTED first, hardening second. Shape behaviour via space; then add locks, glass, bollards.
Rooms matter. Wiring closets and server rooms deserve MFA + fail-secure + two-person rule.
Practice, not posters. Drill evacuations, test generators under load, review access quarterly
Follow the Series - PKI
#CISSP #CyberSecurity #InfoSec #SecurityLeadership #WomenInCyberforce #WomenInTech #AnyaInCyberSecurity #FromDevToDefender #TechLeadership #DevSecOps #CISSPDomains #PhysicalSecurity #CPTED #DataCenter #UptimeInstitute